Search: fišing
National Cyber Conference 2025
The Regulatory Authority for Electronic Communications and Postal Services (RATEL), in the capacity of the National CERT of the Republic of Serbia, and the Serbian National Internet Domain Name Registry Foundation (RNIDS), on 24 October hosted their third joint National Cyber Conference. During the event, current topics in the area of information security were addressed, with the aim of further informing the public about modern threats and risks on the Internet, the importance of preventive responses, methods of protection, education and safer use of the Internet.
The conference was opened with a welcoming speech by Duško Kodžić, Director of the Cyber Security and IT Department at RATEL. In his address, he highlighted the fact that the number of incidents reported to the National CERT in the previous year had increased by more than 70% compared to 2023. He also warned about the growing number of frauds, increasingly sophisticated due to the misuse of artificial intelligence, but also added that the National CERT was working to raise awareness of the general public through education and collaboration with relevant institutions and organizations.
In the opening remarks, the attendees were welcomed by Filip Pavlović, Assistant Minister for International Cooperation and European Integration, and Plamena Halacheva, Deputy Head of the EU Delegation to Serbia.
The opening speeches were followed by two presentations. The Head of the Cybersecurity and National CERT Affairs Division, dr Marko Krstić, emphasized in his presentation the importance of sharing timely and relevant information, announced the development of a section of the web portal dedicated to ICT systems of special importance and presented the activities of the National CERT in the fields of education and awareness-raising, additionally outlining this organization’s further tasks following the adoption of the new Law on Information Security.
In the second presentation, Adel Abusara, Director at PwC Serbia, presented current trends in risk analysis in the area of information security and pointed out the challenges that different types of organizations may encounter in the entire process, from risk monitoring to decision-making.
In the following panel titled Cyber security & AI, participants discussed the dual nature of artificial intelligence: on the one hand, it can be an ally, and on the other, a cyber security challenge. Everyone agreed that artificial intelligence significantly helps in detecting and preventing cyber attacks, but that it can also pose a risk if used without control and supervision. It was also stressed that Serbia is not lagging behind in the trends of AI misuse, a foul practice that makes it ever more difficult to detect scams.
Dijana Milutinović's (RNIDS) interlocutors at the panel Cyber Security Startups in Serbia shared their experiences on the challenges faced by startups in the field of information security in Serbia. The panel concluded that startup success comes through learning, adaptation, and the courage to take risks, which, as they stated, is often more important than technical perfection itself.
The representative of the National CERT of Serbia, Daniela Andrović, presented the annual report on statistical data on all incidents in ICT systems of special importance for 2024, with a review of key statistical indicators and a comparison to the previous year. An analysis of reports to the National CERT in the previous year was also presented, which concluded that there was a surge in phishing campaigns and scams, especially via SMS messages, social networks and messages via communication apps (Viber, Whatsapp).
Vladimir Vujić of the Technical Directorate for Information and Communication Technology of the Ministry of Interior spoke about the state and trends in high-tech crime in the Republic of Serbia. He said that in the future, every form of crime was bound to become high-tech crime, given the widespread digitalization in all areas of life and work. The presentation also featured the most common forms of high-tech fraud, including online scams, ransomware, threats to personal security, and child abuse via the Internet.
The following panel, Capacity building in the field of information security in Serbia, presented the results of cooperation within the ''Cyber Balkans'' project, based on private-public partnerships, where the emphasis was placed on organizing and holding combined cyber exercises in collaboration with the National CERT. Milan Sekuloski's interlocutors presented the conclusions of the exercises held, as well as the perceived challenges that the participants encountered during the training.
In their inspiring stories, the speakers addressed the challenges still persisting in the field of information security, such as the need for greater involvement by the cyber community, the creation of cases dealing with the legal aspects of information security, as well as further investment in youth development.
The recording of the National Cyber Conference is available at the following link.
The conference was organized with the support of the Ministry of Information and Telecommunications, the e-Governance Academy (eGA), and the Cybersecurity Network Foundation.
Phishing campaign abusing the name "Roads of Serbia"
The National CERT warns all citizens that there is a current phishing campaign abusing the name of the public enterprise "Roads of Serbia". Users are being sent fake text messages informing them of a supposedly unpaid traffic ticket.
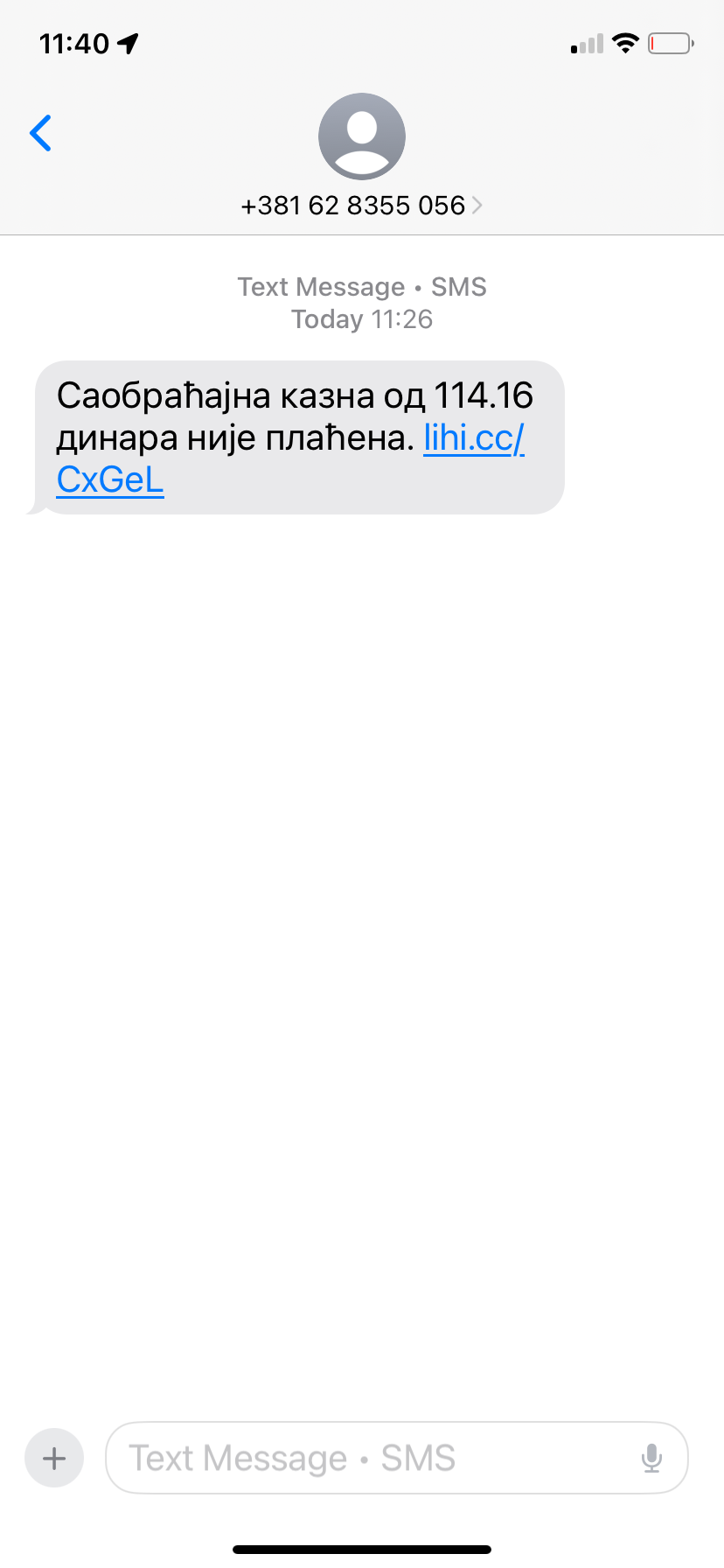
By clicking on the link in the message, the user is redirected to the fake page putevI-srbije.help/rs, where they are asked to provide a phone number and bank card details.
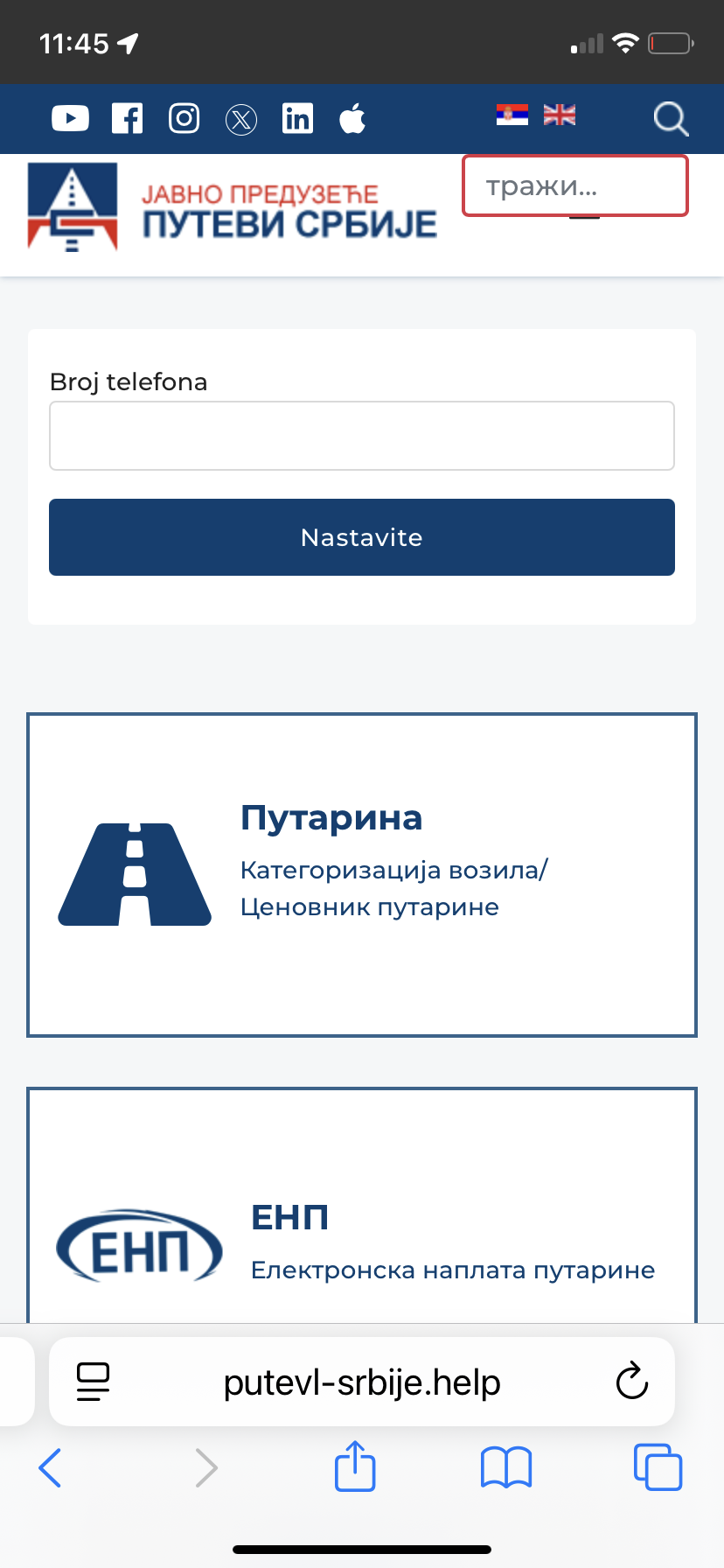
The National CERT recommends that citizens not access links from these messages, and to report the incident if they have been scammed or if they notice an attempted scam.
SPF, DMARC, DKIM
Reduced possibility of spoofing the original Domain
Prevention of potential abuse of the user's email address
The implementation of three email verification mechanisms (SPF, DKIM and DMARK) can significantly reduce the receipt of Phishing messages.
Phishing campaign abusing name of Air Serbia
The National CERT of the Republic of Serbia informs citizens that a new phishing campaign is currently underway, abusing the name of the company Air Serbia.
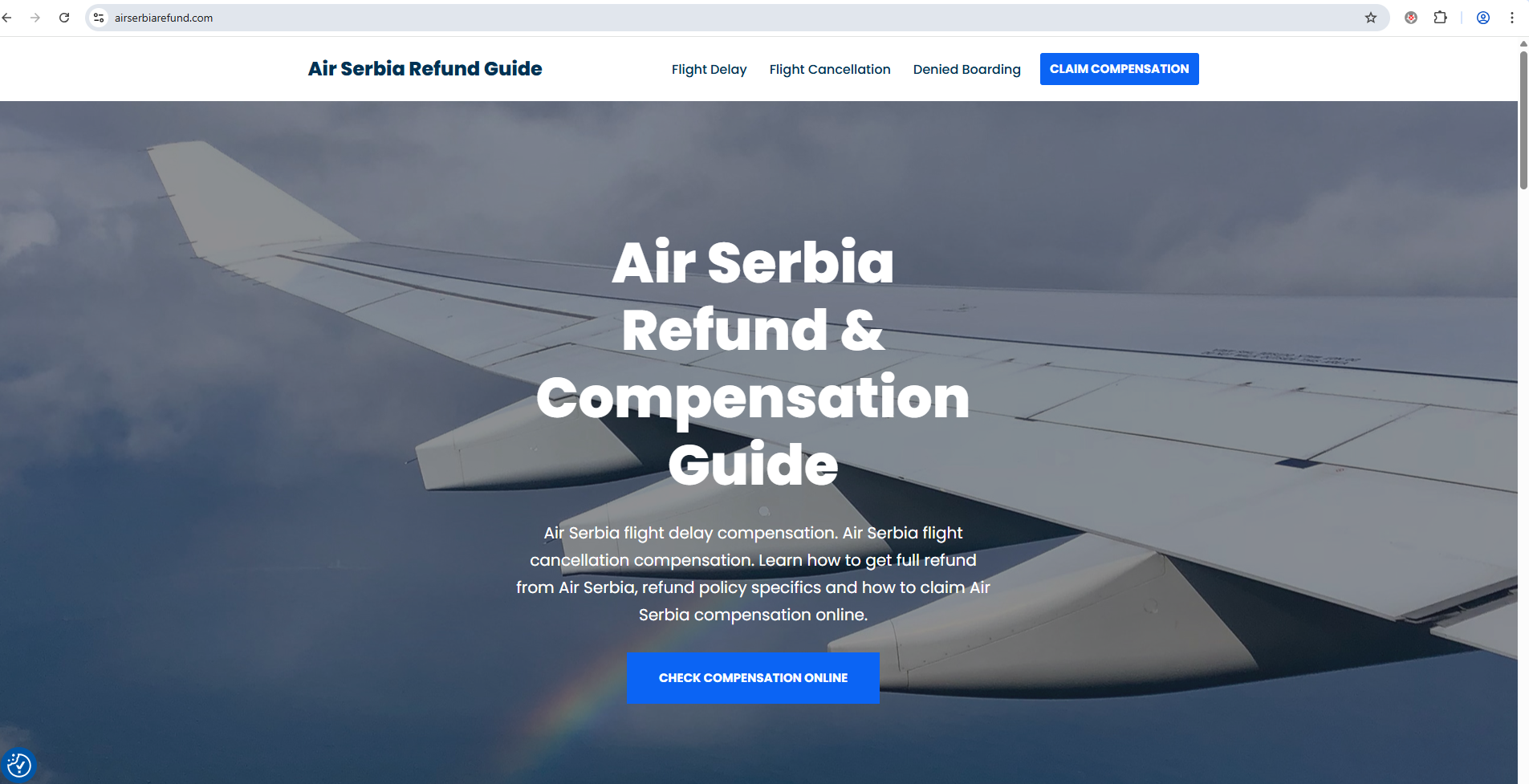
A fraudulent website (https://airserbiarefund.com) has been created that uses the name Air Serbia without authorization. On this fake profile, Air Serbia passengers are offered an alleged reimbursement of expenses.
We caution the public that disclosing personal and financial data on the mentioned website may lead to their misuse.
The National CERT recommends that citizens do not visit the mentioned website and do not enter their data, but rather look for all information related to Air Serbia on the company's official website: https://www.airserbia.com/.
The appearance of the fraudulent website abusing the name of Air Serbia:
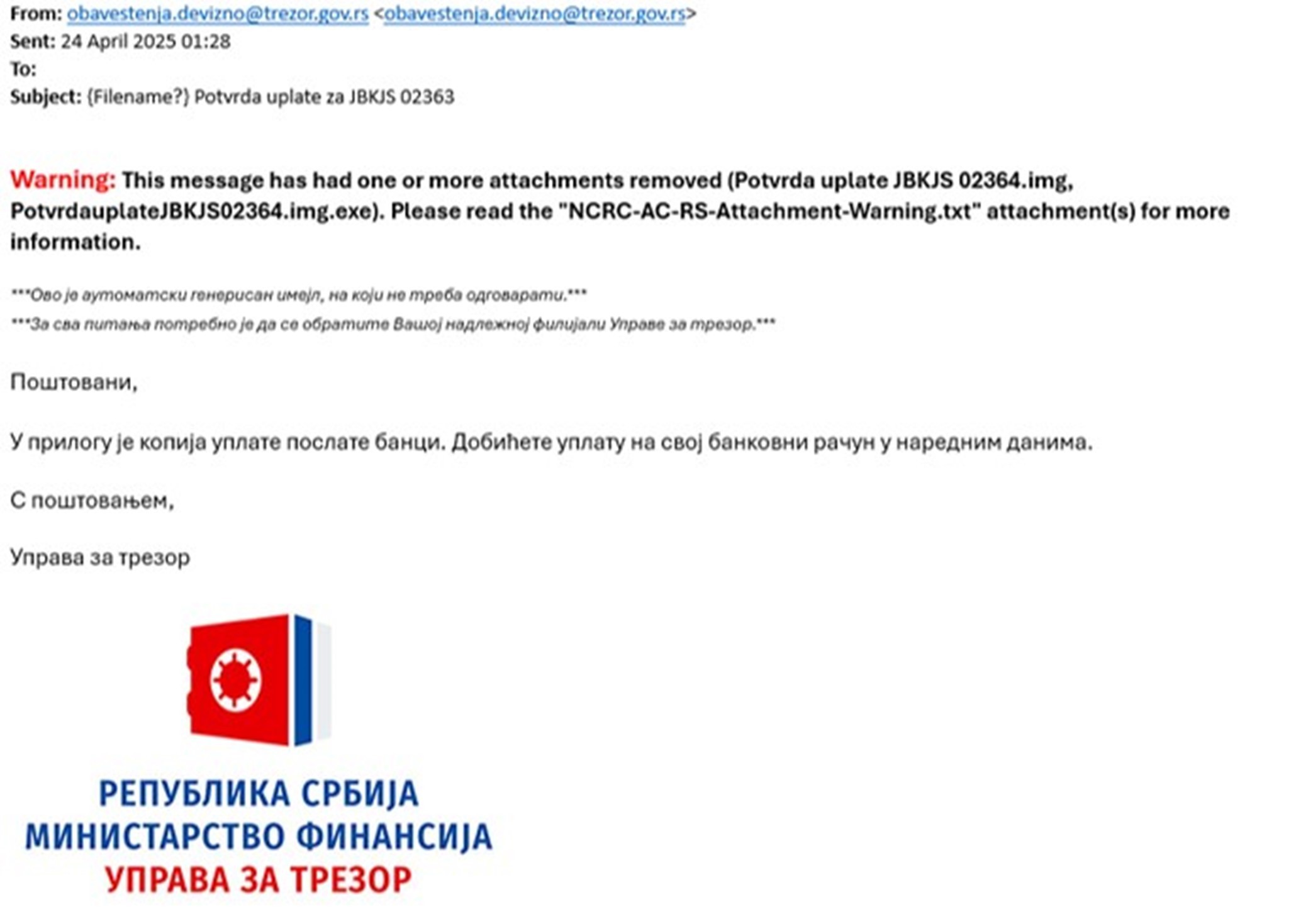
Phishing campaign that misuses the Treasury Administration logo
The Ministry of Finance of the Government of the Republic of Serbia has warned about the misuse of the Treasury Administration email address and urged citizens to carefully check the mail they receive.
The sender misused the Treasury Administration logo and disguised his address as one of the administration's official addresses, so that the malicious email appears to the recipient as if it was sent from the account obavestenja.devizno@trezor.gov.rs.
We warn that the email contains a malicious attachment that should not be opened and we emphasize that all received mail should be carefully checked.
The Treasury Administration, which reported this case to the Department for High-Tech Crime of the Ministry of the Interior, is not behind the emails with the stated content, the statement says.
Vishing and Smishing
- Vishing is a cyber scam that takes place through calls
- Smishing is a cyber scam that starts via SMS or Chat messages
- The most common scams are aimed at collecting personal, business or financial data
COVID-19 phishing campaign
The National CERT wishes to inform the public on the current phishing campaigns abusing COVID-19 virus (coronavirus) alerts.
The campaign is most frequently being realized in the form of email messages containing different types of information related to COVID-19 virus.
In the email body text, the recipient is asked to enter user name and password, in order to supposedly access information on protection measures related to COVID-19.
In addition, the messages can also contain information on other current topics related to coronavirus, such as: infection maps, possible impact on the economy and similar.
The National CERT recommends the users not to enter their credentials in case of such emails.
New phishing campaign that misuses the name of the National Bank of Serbia
The National CERT of the Republic of Serbia informs the public about an ongoing phishing campaign that misuses the name of the National Bank of Serbia.
Scams are being delivered to citizens via email or social media, requesting the entry of personal and financial information, which attackers can use to withdraw funds from citizens' accounts.
The announcement from the National Bank of Serbia is available at the following link.
Cyber frauds during holiday season
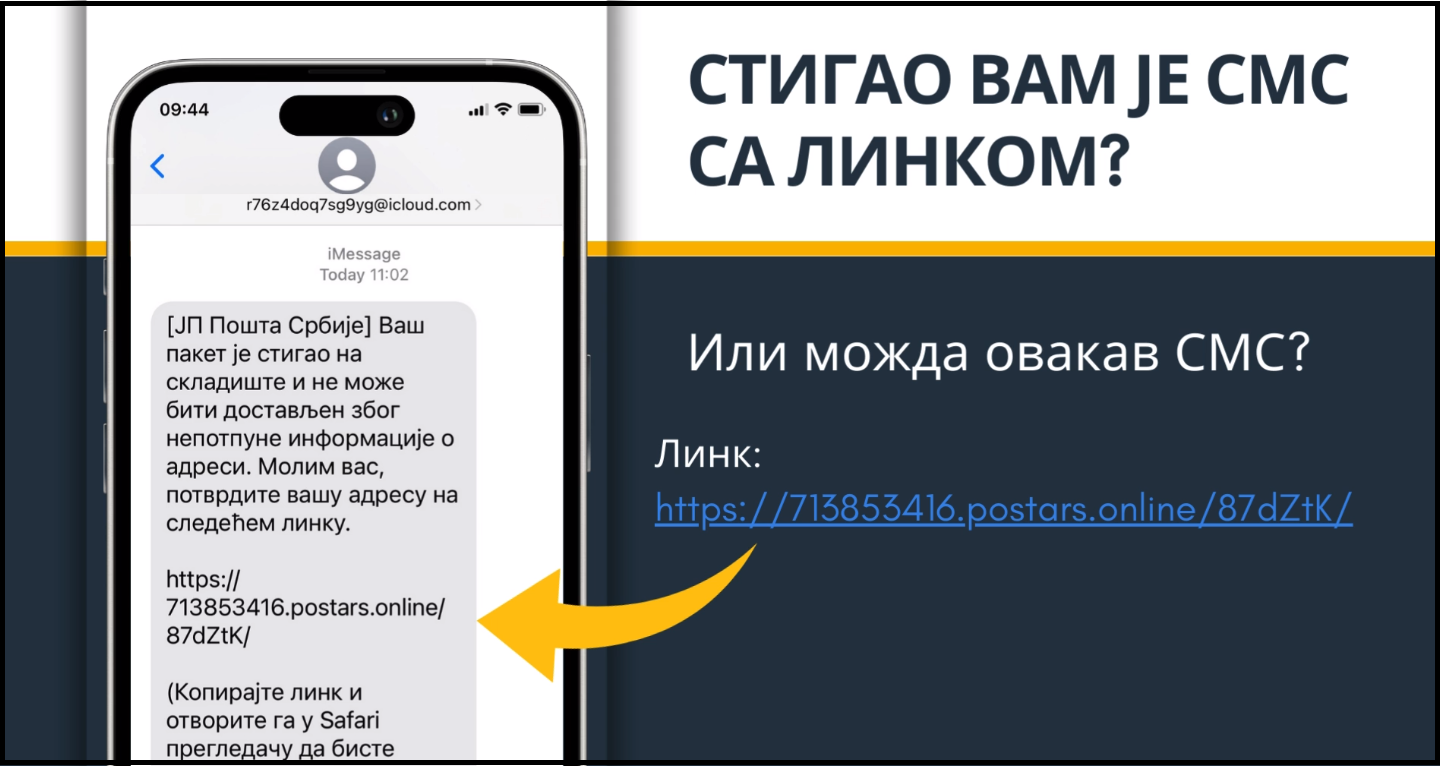
December being traditionally a month of holiday shopping and increased volumes of posted items, it is also a time of a growing number of cyber threat attempts. The National CERT of the Republic of Serbia therefore warns the citizens about current SMS phishing frauds targeting the users of postal services in this time of the year.
The attackers usually initiate the fraud by sending an SMS or text, containing an information about an unsuccessful postal item delivery attempt, along with a link to confirm address details. By clicking on the link, the victim is transferred to a fake web page of the PE Post of Serbia, where they are asked to enter personal information and credit card data. Disclosure of these personal data on the fake web page enables the attackers to clear the victim’s bank account.
The National CERT urges the citizens not to click on links contained in messages from unknown senders and to report similar incidents, in case they were defrauded.
More on this topic can be found in our video: ‘’SMS phishing frauds’’.