Search: fišing
Phishing
- A fraud technique that aims to collect and misuse confidential user data
- A quick reaction of the user is expected - clicking on a link, opening an attachment in an email, accepting a request on Social Networks, etc.
- Carefully open emails from unknown senders
Phishing campaign targeting bank clients in the Republic of Serbia
The National CERT informs all banking customers that a malicious phishing campaign is underway that misuses the name of Raiffeisen Bank, which operates in the market of the Republic of Serbia. This is a campaign that reaches users in the form of email messages with titles such as: "Urgent action is needed for the security of your credit card!" or "You must verify your identity!". The text of the malicious email states that there has been an alleged error in the functioning of the user's account and that it is necessary for the user to update their data, or that unusual use of the payment card has allegedly been noticed and that it has been misused, followed by instructions on what to do to prevent further misuse of the payment card. The message also contains a 12-hour deadline for updating personal data, in order for the user to prevent the alleged blocking of access to the bank account.
Based on past experience, such phishing campaigns are usually distributed on behalf of several different banks operating in the Republic of Serbia, which is why the National CERT recommends that all users, if they receive such e-mails, be cautious and delete them immediately, and especially pay attention not to click on the link in the message or open the attachment. Also, banks usually send such notifications to clients with a digital signature, so it is possible to verify the identity of the sender even before opening the e-mail.
Below, you can find an example of one of such phishing messages, while the publication of Raiffeisen Bank, with examples of spoofed domains, can be seen at the following link.

Phishing scam attempt
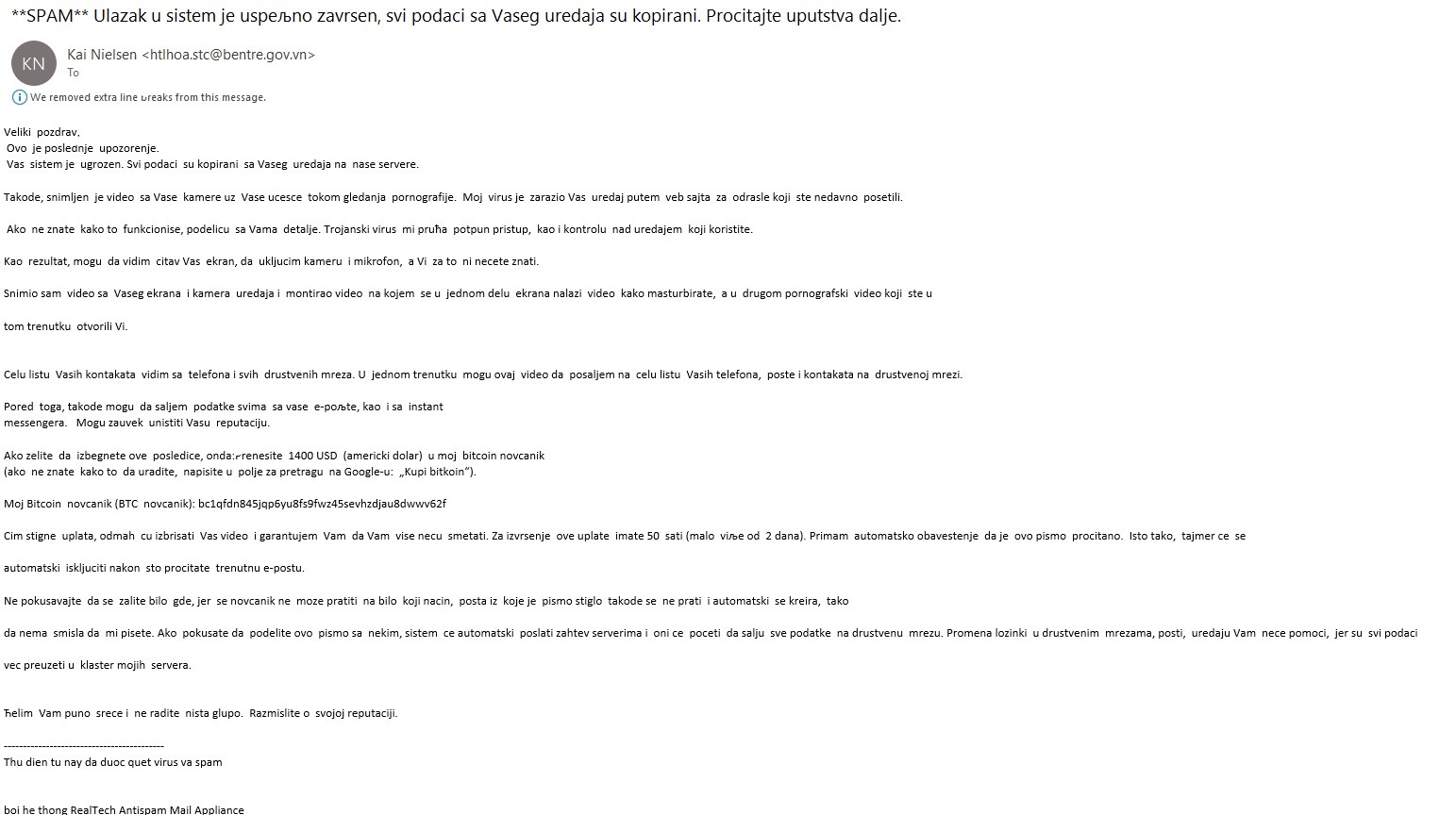
The National CERT of the Republic of Serbia wishes to inform all Internet users of a new ongoing phishing campaign titled „**SPAM** Ulazak u sistem je uspešno završen, svi podaci sa Vašeg uredaja su kopirani. Pročitajte uputstva dalje.“ The phishing message further reads a threatening information about all the user’s data having been copied and locked, and even a video caption of the user been taken, including all of his/her social network contacts. In exchange for the „recovery“ of the stolen data, a Bitcoin payment in the amount of 1400 USD within 50 hours is requested. The message itself does not contain a fake link, but fraudulently influences the user to willingly make a payment in order to recover their data.
The National CERT recommends that all such emails be deleted. Careful scrutiny of similar incoming messages makes it harder for the attackers to take advantage of your lack of attention on the Internet. Users are advised to be particularly watchful when receiving emails from unknown senders, containing grammatical errors, where an immediate action is required from them.
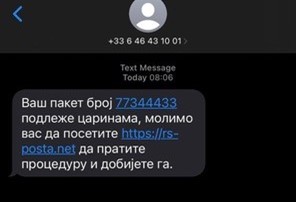
SMS phishing attacks against users of postal services
The National CERT of the Republic of Serbia wishes to inform the public that a new SMS phishing campaign against users of postal services is under way. A fraudulent SMS is sent to the user, saying that a parcel supposedly could not be delivered to them due to an unpaid customs fee, asking them to open the link contained in the text message in order to retrieve their parcel. Fake links currently in circulation are: https://rs-posta.com, https://rs-posta.net, https://posta-serbia.com and https://posta-srbija.com.
The link from the text message leads to a fake page where the user is asked to fill in their bank or credit card details, which ultimately enables the attackers to clear the victim’s bank account.
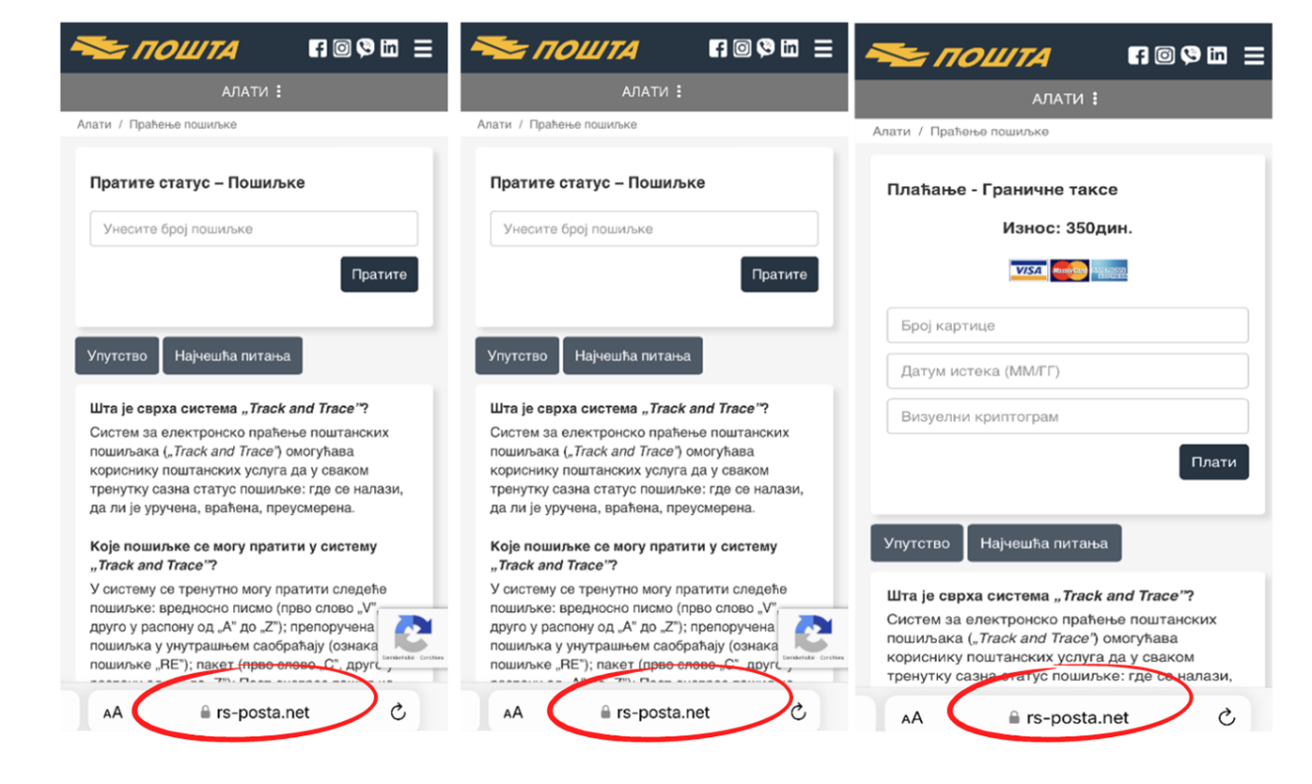
The PE „Post of Serbia“ reminds the public that this is not how this company communicates with its users, therefore extra attention is warranted.
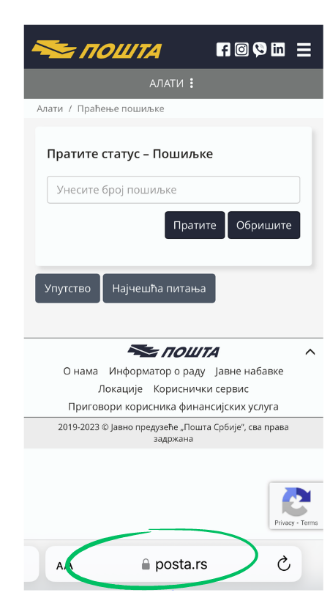
This is how the PE „Post of Serbia“ legitimate page looks like:
The National CERT urges all users who have possibly received such SMS neither to open the link contained therein, nor to disclose their personal data, but to delete such text messages permanently.
On the National CERT’s website, several publications about these threats have been made available, including the way current phishing campaigns are being carried out. In addition, our platform „For a Safer Click“ contains interactive content about various cybersecurity topics.
The above fraud can be reported to the „Post of Serbia“ via the official contact center telephone numbers 0700 100 300 and 011 3607 788, on business days from 8h to 20h and on weekends from 8h to 15h, as well as to the National CERT.
Phishing Campaign Targeting Postal Service Users
The National CERT of the Republic of Serbia wishes to inform and warn all users that a new phishing campaign targeting postal service users is under way. The users usually receive an email notifying them about „unsuccessful“ parcel delivery, due to an unpaid customs fee.
Figure 1 shows an example of an email sent to users:
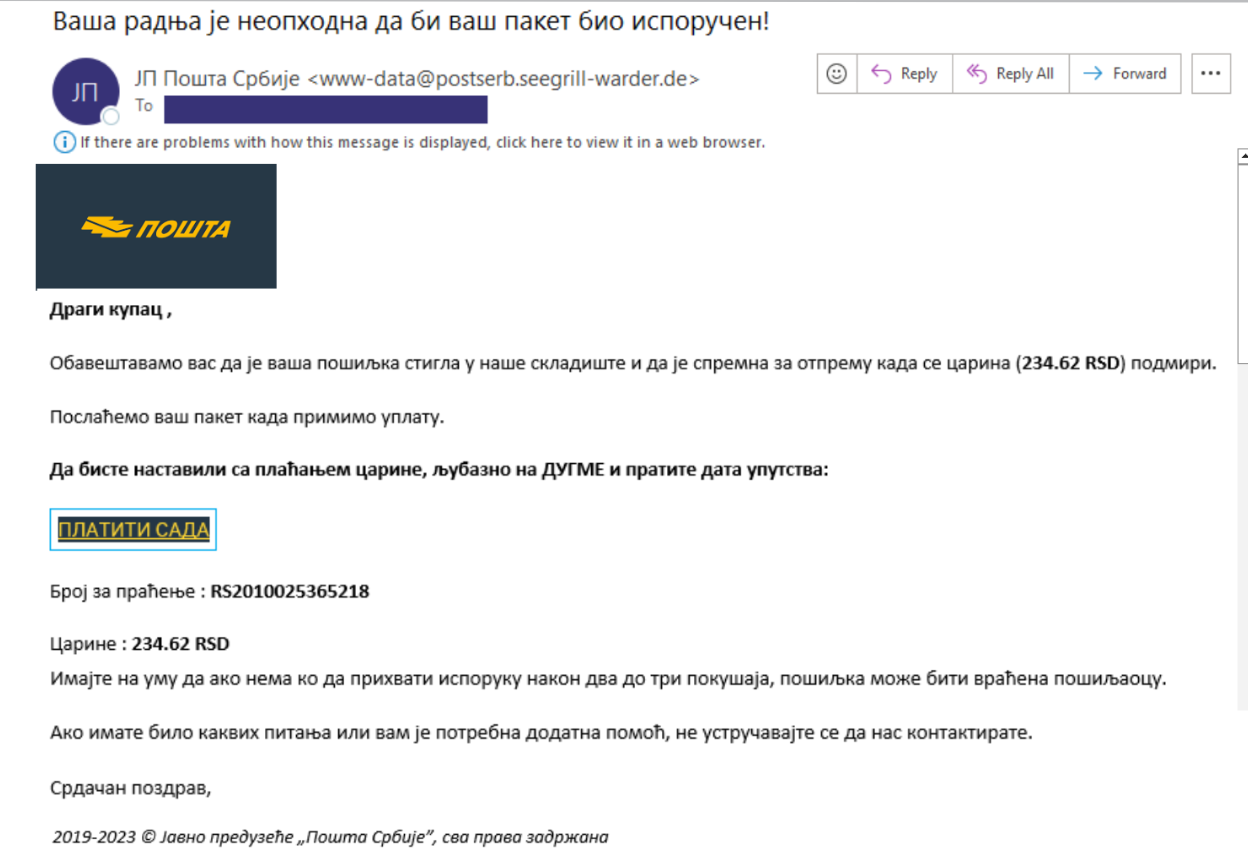 |
Figure 1 – Phishing email example
The user is asked to click on the email link, leading to a fake page of the Post of Serbia, where the user is required to make payment by filling in his credit card information. Figure 2 shows the look of the fake page where the user is asked to make a payment:
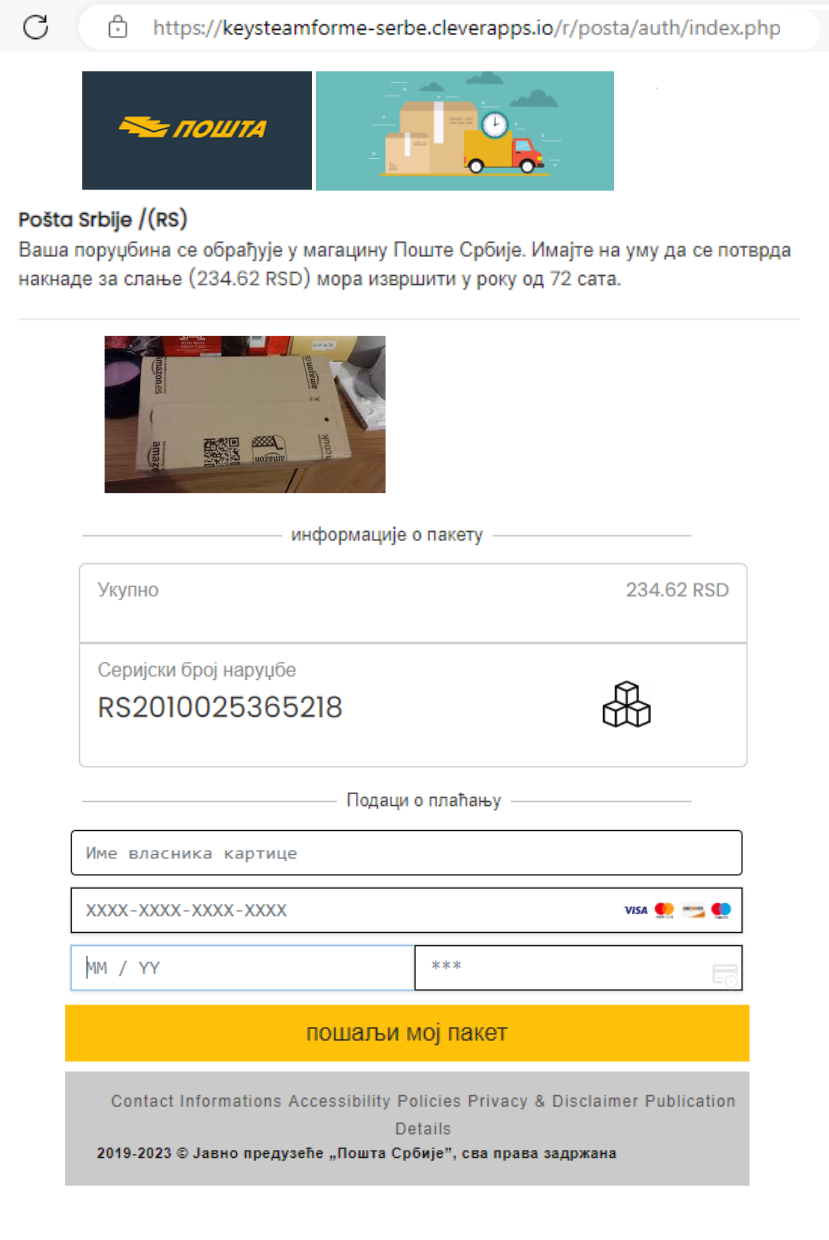 |
Figure 2 – Example of fake payment page
All the information provided by the user on the fake page can be abused. The National CERT recommends to the users who happen to receive such email, not to open it nor enter the required data, but to delete it right away.
The above fraudulent activity can be reported to the „Post of Serbia“ via the official contact center telephone numbers 0700 100 300 and 011 3607 788, on business days from 8h to 20h and on weekends from 8h to 15h, as well as to the National CERT.
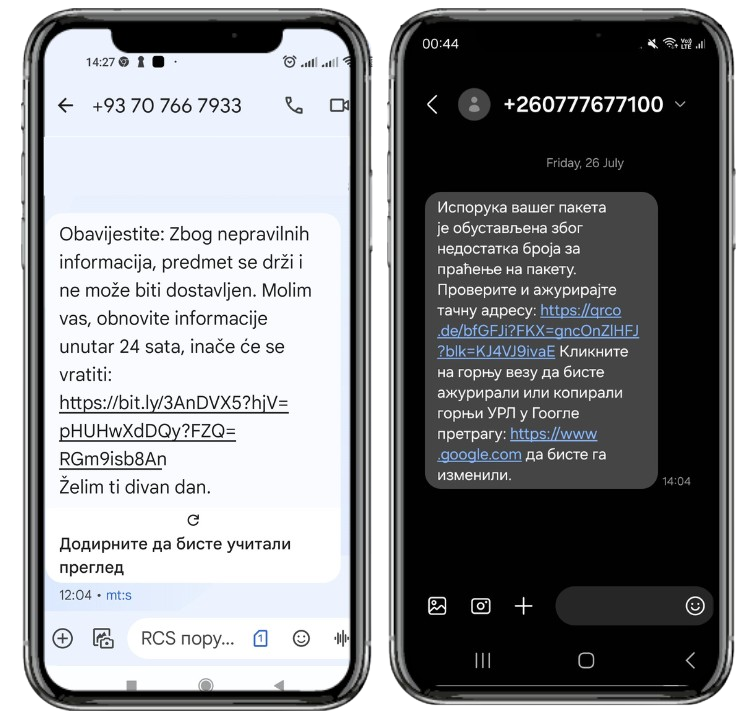
Phishing campaign targeting citizens and postal service users
The National CERT warns all citizens that an SMS phishing campaign is currently underway, which is misusing the name of the PE ''Post of Serbia'' (JP "Pošta Srbije").
Users are sent an SMS message stating that their package could not be delivered due to incomplete address information and that in order to deliver the package, they need to open a link in the message and update their address information.
By clicking on the link, citizens are redirected to a fake website of the Post of Serbia, which requires the entry of personal and payment card information. By entering this information on the fake website, attackers are enabled to withdraw money from citizens' accounts.
The increased volume of purchases due to current seasonal discounts and the increasing popularity of e-commerce applications may also lead to an increase in fraud targeting postal service users.
The National CERT recommends that citizens not click on links in messages received from unknown senders, to use official channels for tracking shipments, and to report an incident if they have been scammed.
In addition, in order to improve the level of security for online purchases, a general recommendation for users is to pay using a special internet card, which is intended exclusively for online payments. In this way, users limit access to the funds available on that card and prevent attackers from taking over the funds that users have in their dinar or foreign currency accounts.
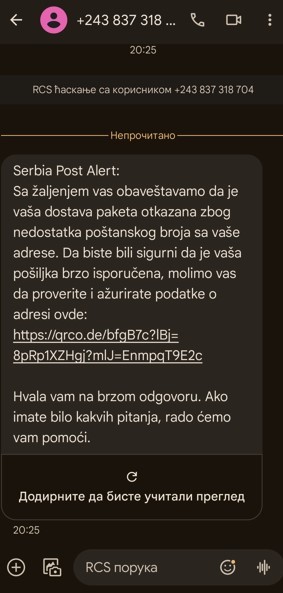
Phishing campaign targeting citizens and postal service users
The National CERT warns all citizens that the phishing campaign misusing the name of the PE ''Post of Serbia'' is currently underway again. The increased volume of purchases due to current seasonal discounts and the increasing popularity of e-commerce applications may also lead to an increase in fraud targeting postal service users.
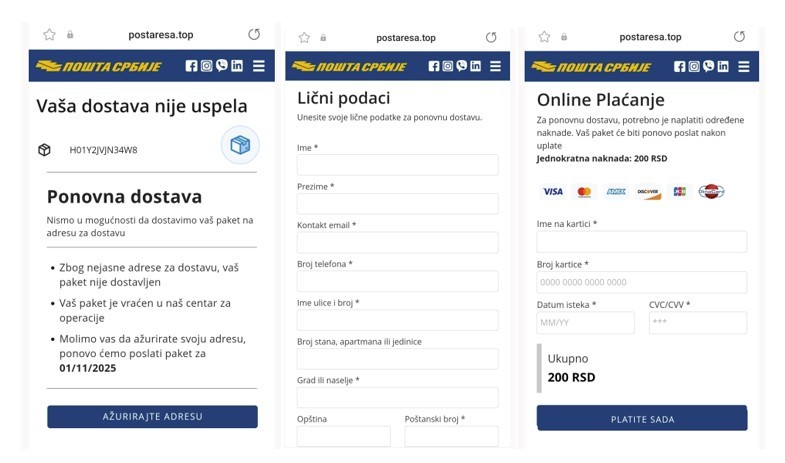
Users are sent an SMS message stating that their package could not be delivered due to incomplete address information and that in order to deliver the package, they need to open a link in the message, update their address information and pay 200 RSD.
By clicking on the link, citizens are redirected to a fake website of the Post of Serbia, which requires the entry of personal and payment card information. By entering this information on the fake website, attackers are enabled to withdraw money from citizens' accounts.
The National CERT recommends that citizens not click on links in messages received from unknown senders, but use official channels for tracking shipments, and report an incident if they have been scammed.
In addition, in order to improve the level of security for online purchases, a general recommendation for users is to make their payments via a special internet payment card, intended exclusively for online payments, whereby they will limit access to the funds available on the card and prevent the attackers from emptying their national or foreign currency bank account.
Phishing scam that abuses user verification option (CAPTCHA)
There are new phishing scams that abuse the verification option (CAPTCHA), i.e. attacks where fake CAPTCHA windows are used to trick users into unknowingly launching malicious software. These attacks often look like legitimate communications from well-known services or platforms.
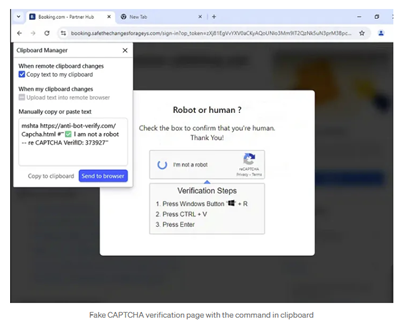
An example of this kind of fraud, which abuses the online accommodation booking platform Booking.com, reaches the user via e-mail. The subject of the message is ''Poor guest experience'' containing a link and clicking on the provided link redirects users to a fake verification website titled ''Robot or human?'' (see image). The provided URL booking.safethechangesforageys.com is not the official domain name of the Booking.com platform. This attacker technique asks the user to:
- Open the Windows Run window,
- Copy the command from the clipboard, and
- Run it by pressing the Enter key.
In this way, the attacker tricks the user into allowing him unauthorized access and misuse of the device. A detailed analysis of the specific example can be found at the link.
As in all previous phishing campaigns, users can independently and without additional technical knowledge recognize that they are being scammed by simply checking the domain name to which they are redirected by clicking on the link. It is recommended that if users are not sure about the legitimacy of the message, they contact customer support via the official website or application and check whether the message is really from them. Additionally, if the user does not use the services of the aforementioned accommodation booking platform (as is the case in this specific example), or does not expect an e-mail from the sender (who is most often unknown), it is recommended that such an e-mail not be opened and deleted.
New phishing campaign targeting bank clients in the Republic of Serbia
The National CERT informs all banking customers that a malicious phishing campaign is underway that misuses the name of Raiffeisen Bank, which operates in the market of the Republic of Serbia. This is a campaign that reaches users in the form of email messages with titles such as: "Important Notice: Your Account is Temporarily Blocked" and "Urgent Update Required: Act Immediately Regarding Your Account". The text of the malicious email states that there has been an alleged significant improvement in the bank's security system and that it is necessary for the user to update their data.
Based on previous experience, such phishing campaigns are distributed on behalf of several banks operating in the territory of the Republic of Serbia. The National CERT recommends that all users, if they receive such messages via email, be cautious and delete them immediately, and it is especially important to pay attention not to click on the link in the message or open the attachment. Also, banks usually send such notifications to clients with a digital signature, so it is possible to verify the identity of the sender even before opening the email.
Below you can see an example of the last of these phishing messages, while Raiffeisen Bank's announcement, with examples of spoofed domains and a detailed, visual, display of how to recognize them, can be seen at the following link.
